>show system info
Thursday, January 22, 2015
PALO ALTO CLI - Checking Software version --OKAY
Wednesday, January 21, 2015
Palo Alto - CLI --- Operation Mode and Configuration Mode OKAY
Palo Alto - Packet Capture --okay
4 State Capture --> 4 difference files
Receive State ---------->Drop State ---------->FW State -------->Transmit (marked to leave firewall)
to check if the packet actually left the FW , check the device on the other side
Packet Capture on GUI
"Monitor" --> " Packet Capture
Pre-Parse Match ---> Never use it
Put a Limit
CLI Capture
debug dataplane packet-diag clear all
debug dataplane packet-diag set filter match
debug dataplane packet-diag set capture stage receive (firewall,transmit, drop) file rx.pcap
debug dataplane packet-diag set capture off
debug dataplane packet-diag set capture off
Palo Alto Models
PA200
PA500
PA3000
PA5000
PA 7000
PA500
PA3000
PA5000
PA 7000
Packet Flow Sequence in PAN-OS
Palo Alto Networks next-generation firewalls use a unique Single Pass Parallel Processing (SP3) Architecture – which enables high-throughput, low-latency network security, all while incorporating unprecedented features and technology
Interface --->L2 to L3 (+NAT)--->App ID --->Content ID --->
**NAT***
Outbound (Company to Outside)
-Security (INSIDE) 10.x.x.x --- fw----> (OUTSIDE) 172.24.x.x (actual destination)
-NAT Policy (INSIDE) 10.x.x.x ---fw---->(OUTSIDE) 172.24.x.x(actual destination) ---source translation
Inbound (Outside to Company)
-Security (OUTSIDE) 172.24.x.x ----FW-----> (INSIDE) 10.x.x.x
-NAT (OUTSIDE) 172.24.x.x ---FW------> (OUTSIDE) NATIP translation type : destination type (actual IP)
Interface --->L2 to L3 (+NAT)--->App ID --->Content ID --->
**NAT***
Outbound (Company to Outside)
-Security (INSIDE) 10.x.x.x --- fw----> (OUTSIDE) 172.24.x.x (actual destination)
-NAT Policy (INSIDE) 10.x.x.x ---fw---->(OUTSIDE) 172.24.x.x(actual destination) ---source translation
Inbound (Outside to Company)
-Security (OUTSIDE) 172.24.x.x ----FW-----> (INSIDE) 10.x.x.x
-NAT (OUTSIDE) 172.24.x.x ---FW------> (OUTSIDE) NATIP translation type : destination type (actual IP)
Tuesday, January 20, 2015
Palo Alto - Custom Signatures
Make a signature to identity the traffic
Patterns , Context , Decoders
Wireshark to identify signatures .
=============
Custom App-IDs
• To identify proprietary applications.
• To achieve granularity of visibility and control over traffic particular to your environment. If your traffic is classified as unkown-tcp/udp, HTTP or SSL, you could bring visibility by developing custom App-IDs.
• To identify ephemeral apps with topical interest.
o Ex: ESPN3-Video for soccer world cup, March Madness, Wikileaks.
• To identify nested applications.
o Further Identify Facebook-apps – Farmville, chat, marketplace, etc.
• To perform QoS for your specific application.
• URL filtering is incapable of providing control to administrators on websites that replicate on a different host, emulating the same look-n-feel as well as content. Example: wikileaks.com
-------Creating Custom Signature DOC5534
Step1 : Packet Capture
Patterns , Context , Decoders
Wireshark to identify signatures .
=============
Custom App-IDs
• To identify proprietary applications.
• To achieve granularity of visibility and control over traffic particular to your environment. If your traffic is classified as unkown-tcp/udp, HTTP or SSL, you could bring visibility by developing custom App-IDs.
• To identify ephemeral apps with topical interest.
o Ex: ESPN3-Video for soccer world cup, March Madness, Wikileaks.
• To identify nested applications.
o Further Identify Facebook-apps – Farmville, chat, marketplace, etc.
• To perform QoS for your specific application.
• URL filtering is incapable of providing control to administrators on websites that replicate on a different host, emulating the same look-n-feel as well as content. Example: wikileaks.com
-------Creating Custom Signature DOC5534
Step1 : Packet Capture
Palo Alto CLI okay
> debug sslmgr statistics
show config running
set cli config-output-format set
===========
configure
[edit]
student53 #
#load config from ?
# load config from PAN-EDU-311.xml
shows various config available to load
=================
set shared server-profile radius PAN-Radius server DC1 secret pan123
commit
# exit
>
=============
show
test
set
debug
find command keyword fpga
find command keyword radius
find command keyword snmp
=======show session ? =======
show session all
show session info
=======show system disk-space
show system disk quotas
===show counter global
show counter global filter
show country global filter delta yes
==== show counter interface
show session id 1867
=====show running resource-monitor
show running security-policy
show running nat-policy
show running rule-use type used rule-base security vsys vsysl
show running rule-use type unused rule-base security vsys vsysl
show system resources
show system resoruc
show session meter
show session rematch
======show system software status
====show system services
candidate config
tftp import configuration from 10.30.11.153 file PAN-EDU-311-config0-53.xml
show config running
set cli config-output-format set
===========
configure
[edit]
student53 #
#load config from ?
# load config from PAN-EDU-311.xml
shows various config available to load
=================
set shared server-profile radius PAN-Radius server DC1 secret pan123
commit
# exit
>
=============
show
test
set
debug
find command keyword fpga
find command keyword radius
find command keyword snmp
=======show session ? =======
show session all
show session info
=======show system disk-space
show system disk quotas
===show counter global
show counter global filter
show country global filter delta yes
==== show counter interface
show session id 1867
=====show running resource-monitor
show running security-policy
show running nat-policy
show running rule-use type used rule-base security vsys vsysl
show running rule-use type unused rule-base security vsys vsysl
show system resources
show system resoruc
show session meter
show session rematch
======show system software status
====show system services
candidate config
tftp import configuration from 10.30.11.153 file PAN-EDU-311-config0-53.xml
Palo Alto Decryption
Internal Users ------> Request SSL Connection ---------> External Server
Server sends its certificate to FW ----> (FW decrypts the request )generate certificate internally and send request to internal user
Inbound SSL Inspection
Server sends its certificate to FW ----> (FW decrypts the request )generate certificate internally and send request to internal user
Inbound SSL Inspection
Palo Alto - File Blocking with Wildfire
Monday, January 19, 2015
Palo Alto - Antivirus Profile
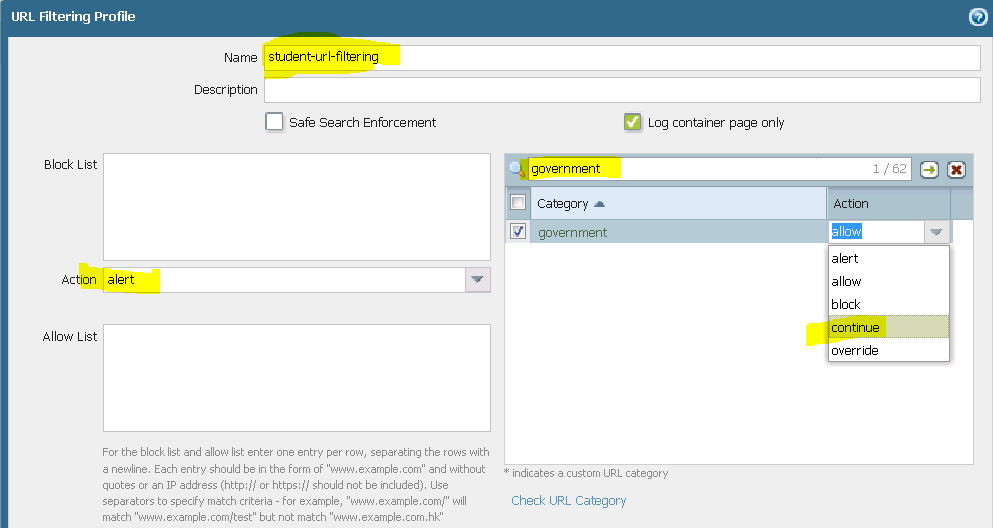
Palo Alto - URL Filtering Profile
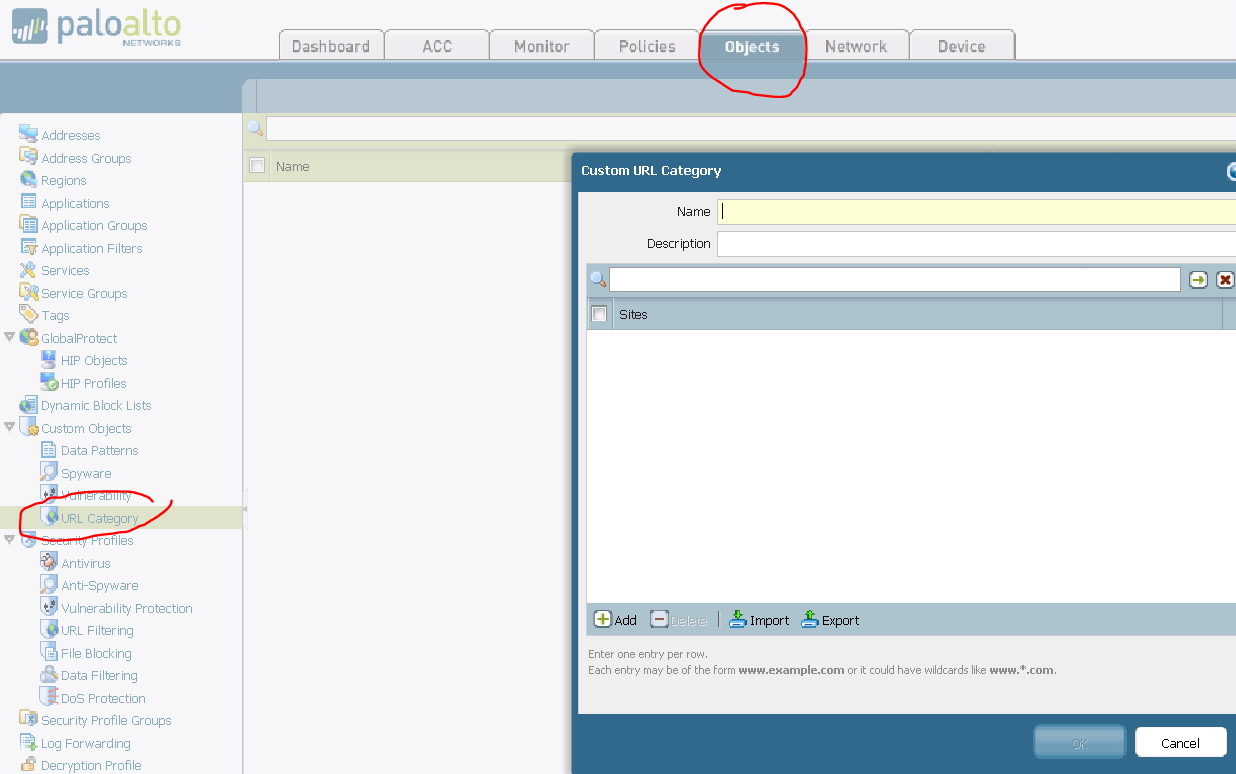
Palo Alto - Adding Custom URL Category
palo
Accredired confiration
CNSE network security engineer (CNSE)
CNSE network security engineer (CNSE)
Subscribe to:
Posts (Atom)